Here’s a short step-by-step guide on how to create and install a self-signed SSL certificate for testing purposes in webMethods Integration Server. You can test secure HTTPS connections from clients to Integration Server with this certificate.
Create a certificate
You can easily create the certificate using OpenSSL on a Linux system.
- Create a private key.
openssl genrsa -des3 -out integrationserver.key 1024 Generating RSA private key, 1024 bit long modulus ........................++++++ .++++++ e is 65537 (0x10001) Enter pass phrase for integrationserver.key: Verifying - Enter pass phrase for integrationserver.key: - Create a certificate signing request (CSR).
openssl req -new -key integrationserver.key -out integrationserver.csr Enter pass phrase for integrationserver.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:DE State or Province Name (full name) [Some-State]:Lower-Saxony Locality Name (eg, city) []:Vechta Organization Name (eg, company) [Internet Widgits Pty Ltd]:Macke IT Organizational Unit Name (eg, section) []: Common Name (eg, YOUR name) []:localhost Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []:IntegrationServer An optional company name []: - Sign the CSR yourself and create a certificate.
openssl x509 -req -days 365 -in integrationserver.csr -signkey integrationserver.key -out integrationserver.crt Signature ok subject=/C=DE/ST=Lower-Saxony/L=Vechta/O=Macke IT/CN=localhost Getting Private key Enter pass phrase for integrationserver.key: - Convert the certificate to DER (which Integration Server needs).
openssl x509 -in integrationserver.crt -inform PEM -out integrationserver_der.crt -outform DER - Create a keystore containing the private key and the certificate in format PKCS12 (which Integration Server needs).
openssl pkcs12 -export -des3 -in integrationserver.crt -inkey integrationserver.key -out integrationserver.pkcs12 Enter pass phrase for integrationserver.key: Enter Export Password: Verifying - Enter Export Password: - Take a look at all the generated files and copy them over to a directory where IS can access them.
ls -la -rw-r--r-- 1 root root 818 10. Jan 18:32 integrationserver.crt -rw-r--r-- 1 root root 680 10. Jan 18:32 integrationserver.csr -rw-r--r-- 1 root root 563 10. Jan 18:34 integrationserver_der.crt -rw-r--r-- 1 root root 963 10. Jan 18:29 integrationserver.key -rw-r--r-- 1 root root 1581 10. Jan 18:34 integrationserver.pkcs12
Install the certificate in Integration Server
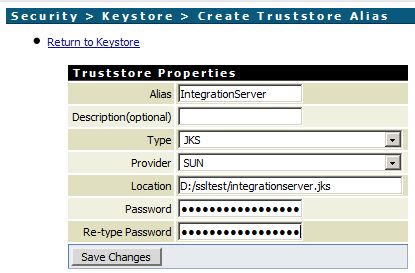
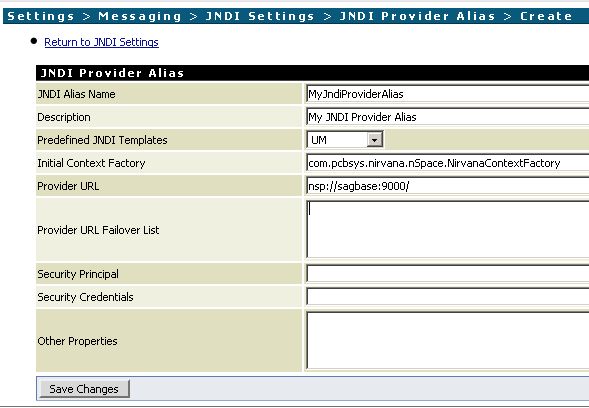
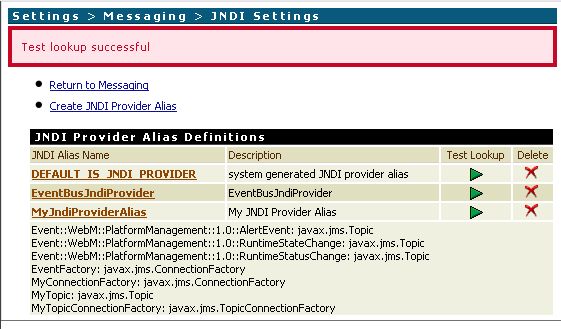
- Install the keystore via Security -> Keystore -> Create Keystore Alias on IS’s web frontend.
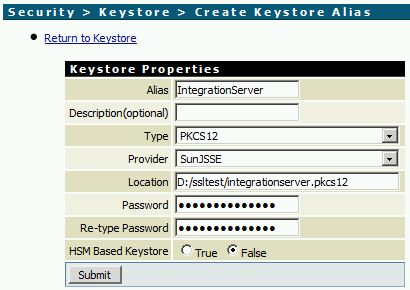
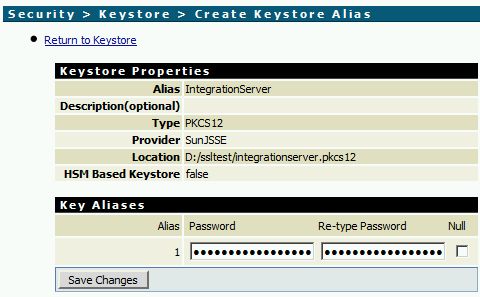
The new Keystore should now be listed.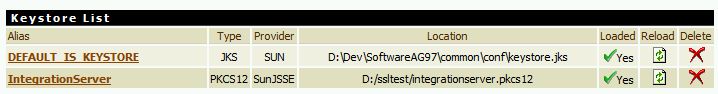
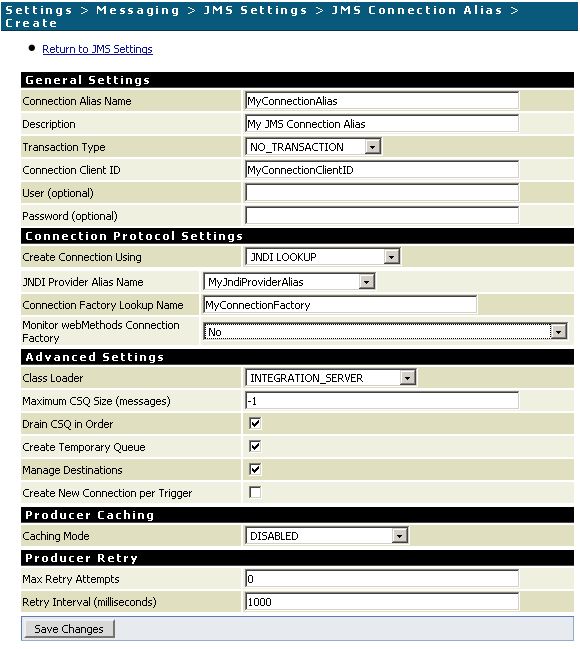
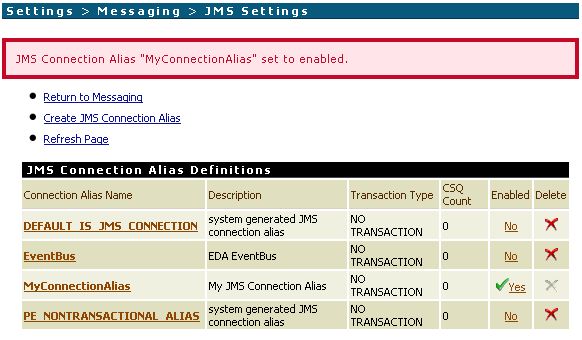
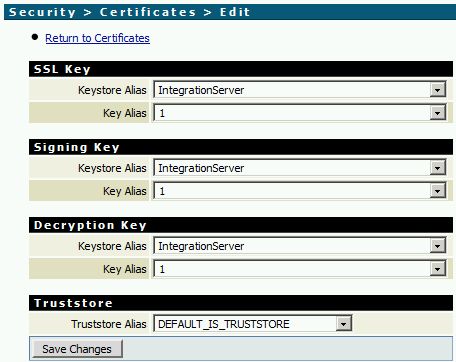
- Install the certificate via Security -> Certificates -> Edit Certificates Settings.
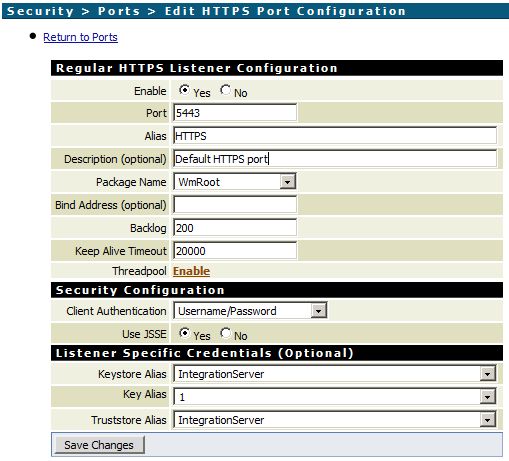
Add an HTTPS Port in Integration Server
- Security -> Ports -> Add Port
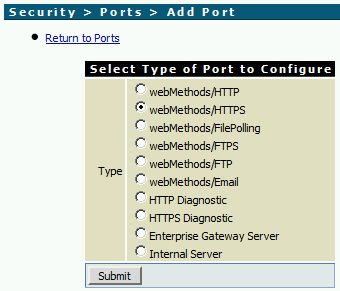
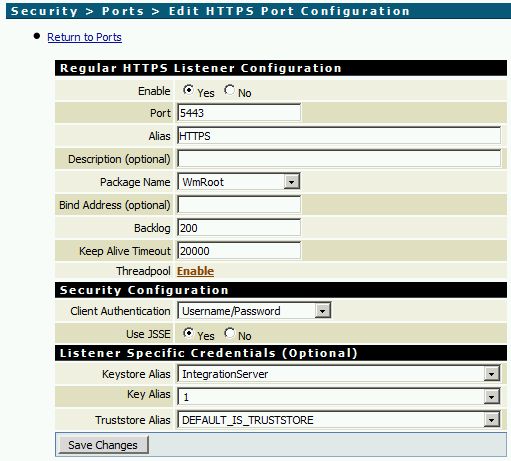
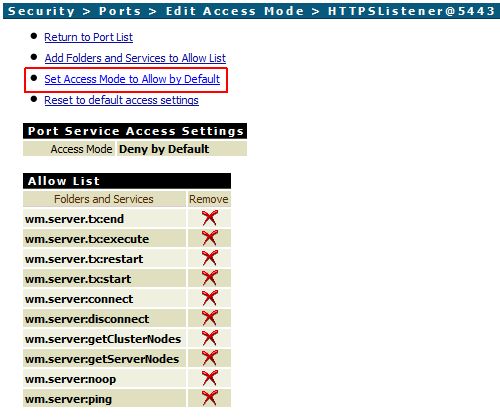
- You may need to configure the Access Mode of the new port, so that folders and services will be available via HTTPS. Simply click on the link in column Access Mode and configure the settings (Security -> Ports -> Edit Access Mode).
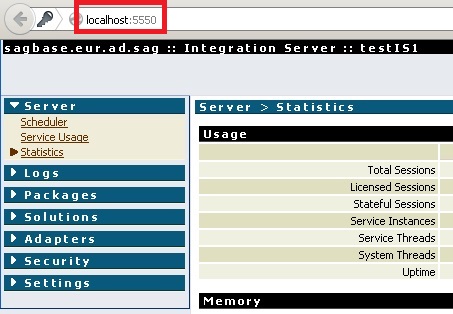
- Test the HTTPS connection by navigating to
https://localhost:5443. The certificate error is ok, because we self-signed our certificate. Add the certificate to the list of trusted certificates and move on. If you use a “real” certificate later, the error will go away.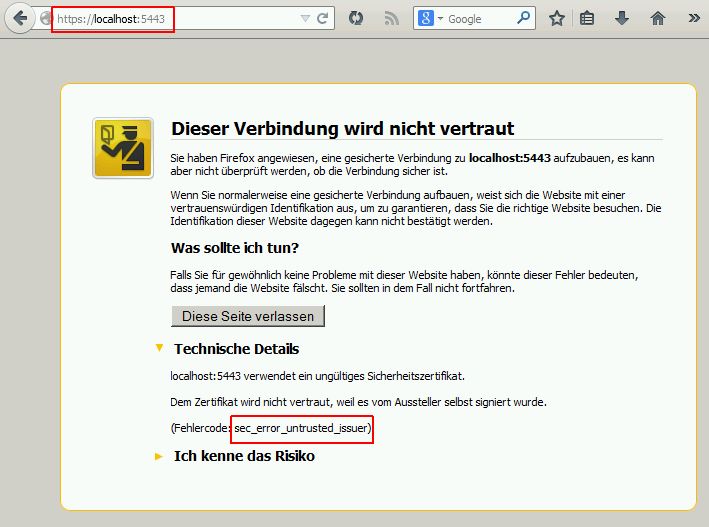
Reference: http://serviceorientedarchitect.com/tag/webmethods-integration-server/